The average enterprise uses well over 100 tools across its stack—each one potentially requiring a license, subscription, or recurring service contract. Combine this sprawling martech ecosystem with decentralized teams, automated accounting systems, and often fragmented procurement workflows, and you have the perfect breeding ground for a growing threat: fraudulent invoicing scams.
These scams are no longer limited to crude phishing attempts or poorly worded emails. Modern fraudsters have evolved, now sending fake invoices through branded PDF attachments, PayPal and QuickBooks requests, and even SMS text messages—some so convincing that even vigilant employees struggle to spot them.
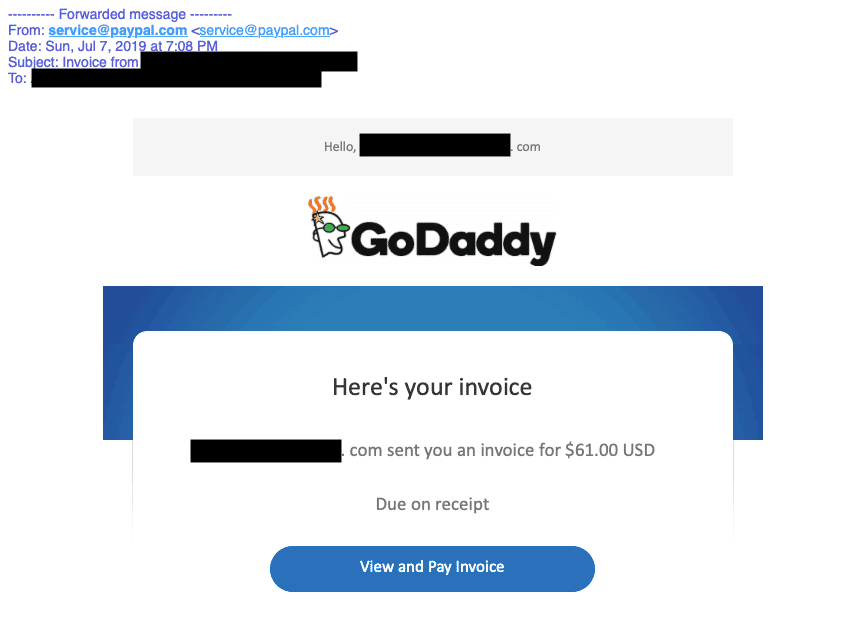
With companies spending tens of thousands to millions of dollars on Martech and vendor relationships annually, attackers know they only need a small crack in the process to exploit. So how can you defend your organization—whether a small business or a sprawling enterprise—against this rising tide of fake invoices and financial deception?
This guide examines the methods companies are employing to combat invoice fraud, including practical policies, technology solutions, and behavioral protocols designed to mitigate the most common attack vectors.
Table of Contents
Why Invoice Fraud Is Booming
First, it helps to understand why marketing organizations are particularly susceptible:
- Numerous vendors: Companies routinely pay for design platforms, automation tools, CRM systems, data vendors, email services, SEO tools, advertising platforms, and dozens of integrations—each with its billing cycles.
- Distributed decision-makers: With decentralized budgets and distributed teams, it’s often unclear who authorized which tool or payment.
- Automated payments: Credit cards on file, recurring billing, and accounts payable (AP) automation systems facilitate the processing of numerous transactions with minimal oversight.
- Branded impersonation: Scammers can easily mimic legitimate invoices from PayPal, Stripe, Zoho, or QuickBooks, exploiting brand trust to deceive staff.
Let’s now examine how companies are protecting themselves from these attacks.
Enforce Strict Vendor Onboarding and Approval Processes
One of the best defenses begins at procurement. Companies should create an internal vendor approval checklist that includes:
- Verification of the vendor’s domain and legal identity
- Confirmation of EIN, W-9, and business registration (if U.S.-based)
- Review of who internally requested the service and for what purpose
- A designated contact person for all billing-related inquiries
Additionally, require that new vendors go through a centralized process managed by Procurement or Accounts Payable. Avoid allowing any employee to add vendors or subscriptions ad hoc without documentation.
Use Unique Invoice Submission Email Addresses Per Vendor
Companies using Google Workspace or Microsoft 365 can create custom email aliases for each vendor. For instance:
invoice+vendor123@yourdomain.com
invoice+hubspot@yourdomain.com
invoice+mailchimp@yourdomain.comBy assigning a unique alias to each vendor:
- You can track who is sending the invoice and detect impersonators
- You can easily create rules to flag or block unknown senders using those aliases
- You reduce the exposure of your primary AP inbox to phishing attempts
This system also provides an audit trail, allowing for better filtering and logging.
Implement Advanced Email Security Filtering
Most phishing invoices arrive via email. While basic spam filters are built into Google and Microsoft platforms, advanced email security solutions can help catch sophisticated threats that slip through.
Recommended solutions include:
- Proofpoint: Offers deep URL and attachment scanning, threat intelligence, and protection against impersonation.
- Mimecast: Adds brand spoof detection, domain similarity analysis, and targeted threat protection.
- Email Security: Focuses on impersonation prevention and real-time threat detection.
These tools utilize AI and machine learning (ML) to identify red flags, such as sender domain mismatches, metadata inconsistencies, and deceptive formatting, thereby significantly improving your odds of interception.
Train Employees on Modern Phishing and Invoice Scams
Your staff is your last line of defense—and also your greatest vulnerability. Many fake invoices are now disguised as:
- A PayPal or Stripe invoice with a real logo and real-looking billing details
- A QuickBooks payment request sent by email or SMS
- A branded PDF invoice requesting payment via ACH
To combat this, regular training should be implemented covering:
- How to verify sender addresses and URLs
- Why not to click on links in unsolicited emails or texts
- How to report suspected fraud attempts to your IT or security team
- The process for validating invoices with finance before payment
Companies using platforms like Cofense can simulate real phishing scenarios to improve awareness.
Use Virtual or Temporary Credit Cards Per Vendor
Virtual card platforms like FinUp allow you to generate vendor-specific credit cards with the following benefits:
- Limit exposure: If a card is compromised, it can’t be used outside the designated vendor.
- Spend control: Set caps or expiration dates on each card.
- Real-time alerts: Get notified of every charge, enabling immediate fraud response.
This method isolates each vendor’s billing relationship and prevents them from accessing shared corporate card numbers.
Block SMS Invoice Threats at the Device or Network Level
Mobile-based scams are growing fast, especially as employees receive invoice requests via SMS or messaging apps like WhatsApp. To reduce this attack vector:
- Implement mobile device management policies that block suspicious links
- Encourage employees to avoid using personal phones for finance-related work
- Prohibit payments or invoice approvals over SMS or mobile apps unless verified via a separate channel
- Use DNS filtering to block malicious domains before they resolve on mobile devices
Maintain a Vendor Directory with Verified Billing Contacts
Establish and maintain a centralized list of approved vendors that includes:
- The legitimate sending domain and email address
- Expected billing frequency and method (e.g., monthly via Stripe)
- Internal owner/contact for the relationship
- Notes on how to verify authenticity
This allows any invoice to be quickly cross-checked against known vendor details. AP or Finance teams should never pay an invoice that can’t be matched to an approved vendor.
Require Invoice Verification for New or Changed Payment Instructions
One of the most dangerous forms of fraud occurs when a known vendor’s payment details are spoofed or intercepted. For example, a scammer might email a new wire transfer number or bank account, pretending to be the vendor. Best practices include:
- Always verify payment changes by calling a known phone number for the vendor
- Use encrypted communication for sensitive payment information
- Require internal approval for any change to payment instructions or routing numbers
Integrate Invoicing with a Secure AP or ERP System
Whenever possible, avoid paying from emailed invoices. Instead, vendors should submit invoices through:
- A secure portal
- An integrated ERP or procurement platform with multi-step validation
- A managed workflow that allows budget holders and AP to approve jointly
By removing the inbox from the equation, you dramatically reduce the surface area for fraud.
Monitor for Emerging Fraud Trends
Finally, this threat landscape is evolving. Monitor:
- New fraud reports shared by your email security provider or IT team
- Updates from the FBI’s Internet Crime Complaint Center
- Alerts from platforms like PayPal, Stripe, or QuickBooks, warning of spoofing campaigns
Fraud tactics shift quickly—what works today may be obsolete in six months. Staying informed is as essential as locking down systems.
Takeaways: How to Defend Against Invoice Scams
- Verify all vendors: Use documented onboarding and verification processes.
- Segment email communication: Use alias addresses per vendor and strong filters.
- Never click invoice links: Open vendor portals manually or via bookmarks.
- Train your team: Regularly simulate invoice scams and reinforce reporting protocols.
- Isolate payment methods: Use virtual cards or locked-down bank accounts per vendor.
- Validate payment details: Call to confirm any changes—not via email.
- Route invoices through secure systems: Avoid inbox approvals.
- Stay ahead of threats: Subscribe to threat intelligence and vendor alerts.
Invoice fraud will continue to evolve—especially as Martech stacks grow more complex. However, by implementing a layered security approach that incorporates process controls, technology safeguards, and ongoing education, you can significantly reduce your company’s exposure and avoid becoming the next victim.
If your company is already managing hundreds of tools or services in marketing and beyond, now is the time to audit your current invoicing and procurement workflows for gaps—and put protections in place before the next fake invoice slips through.